During the research for my master thesis on IoT forensics: “Internet of Things: Traces, Vulnerabilities and Forensic Challenges” (more about it in the future), I found one vulnerability in the QBee Multisensor Camera (https://qbeecam.com/).
CVE-2018-16225 The QBee MultiSensor Camera through 4.16.4 accepts unencrypted network traffic from clients (such as the QBee Cam application through 1.0.5 for Android and the Swisscom Home application up to 10.7.2 for Android), … https://t.co/AV1GX6Uy7e
— CVE (@CVEnew) September 18, 2018
The compatible applications, QBee Cam and Swisscom Home App, by default communicate in cleartext with the camera when on the local network (Testing was done mainly on Android).
The cleartext requests sent to the camera contain the cookies valid to authorize the requests to the camera.
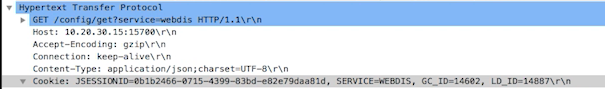 One of these requests is made periodically in background to “/verify”, likely in an attempt to establish an heartbeat.
One of these requests is made periodically in background to “/verify”, likely in an attempt to establish an heartbeat.
By intercepting and reusing the cookies it is possible to send custom commands to the camera; an attacker with access to the local network would therefore be able to disable the camera without the user noticing.
It is also possible to enable the privacy mode (thus disabling the camera) and disable the functionality of the physical button to toggle the privacy mode.
In this case if the user uses the Swisscom Home App, the result is a complete DoS of the camera until a factory reset; this is because that application doesn’t have the ability in the settings to reactivate the functionality of the privacy button, and the privacy mode cannot be disabled from the application.
Video
A video describing the vulnerability is available here: https://youtu.be/dd8vt0_DJF4
Report
PoC
Timeline
08.06.2018 – Vendor contacted (Swisscom & QBee)
11.06.2018 – Acknowledgement from Swisscom & disclosure to Swisscom CSIRT
03.07.2018 – Received response from Vestiacom (QBee) CEO, following communication problems & disclosure to Vestiacom; acknowledgement from Vestiacom that Swisscom already forwarded the problem.
30.08.2018 – CVE-ID obtained from MITRE
30.08.2018 – Vulnerability disclosure date postponed from 9th September to 16th September following Swisscom request
13.09.2018 – Vestiacom confirms the patched version of QBee Cam has been submitted to the iOS App Store (1.5.2) and to Askey for publishing on Android’s Google Play.
16.09.2018 – Public disclosure
Remarks: It was not possible to contact Askey directly as all the public email addresses were non functional, the vulnerability disclosure was handled in collaboration with Swisscom (Swiss reseller of QBee Multisensor Camera) and Vestiacom.
Summary
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 |
[Description] The QBee MultiSensor Camera through 4.16.4 accepts unencrypted network traffic from clients (such as the QBee Cam application through 1.0.5 for Android and the Swisscom Home application up to 10.7.2 for Android), which results in an attacker being able to reuse cookies to bypass authentication and disable the camera. [VulnerabilityType Other] Auth bypass using cookie [Vendor of Product] QBee, Vestiacom, Swisscom [Affected Product Code Base] QBee MultiSensor Camera <= 4.16.4 QBee Cam (Android) <= 1.0.5 (Fixed version number not yet available) QBee Cam (iOS) < 1.5.2 Swisscom Home App (Android) < 10.7.2 Swisscom Home App (iOS) < 10.9.0 [Affected Component] Network Traffic [Attack Type] Remote [Impact Denial of Service] true [Impact Information Disclosure] true [Attack Vectors] Reuse of intercepted cookies to authorize requests to camera and disable it [Has vendor confirmed or acknowledged the vulnerability?] true [Discoverer] Francesco Servida (University of Lausanne) [Reference] https://francescoservida.ch/ https://blog.francescoservida.ch/2018/09/16/cve-2018-16225-public-disclosure-qbee-camera-vulnerability https://unil.ch/esc/ |

Kudos to you for creating such a great website! The content is top-notch, and your post is no exception. It provided me with the exact information I was looking for. Thank you!