The preface of the disclosure of CVE-2018-16225 (https://blog.francescoservida.ch/2018/09/16/cve-2018-16225-public-disclosure-qbee-camera-vulnerability/) contained a little lie: I did not find one vulnerability during the research for my master thesis, but four, three of which were still being patched by the vendor/under the 90 days disclosure timeframe given to the vendor.
In total four vulnerabilities were discovered, concerning the QBee Multisensor Camera (CVE-2018-16223 & CVE-2018-16225) and the iSmartAlarm security device (CVE-2018-16222 & CVE-2018-16224).
[CVE-2018-16222] Cleartext Storage of credentials in iSmartAlarm Android Application
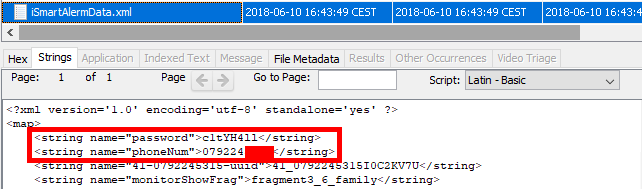
This first vulnerability is pretty simple; the Android application for iSmartAlarm stores the user credentials in cleartext the xml configuration file: iSmartAlermData.xml.
While it is true that an application need to store cloud credentials in order to maintain access to the cloud services, this credentials do not need to be the username and password of the user, but should instead be a revokable access token (Eg. via OAuth).
- CVSS
- Base Score: 6.4
- Vector: AV:P/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H
- Impact Score: 5.9
- Exploitability Score: 0.5
Timeline
08.06.2018 – Vendor contacted
28.06.2018 – Established contact and disclosure to vendor
30.08.2018 – CVE-ID obtained from MITRE
14.09.2018 – iSmartalarm confirms the application is fixed and publication is set for week following
31.10.2018 – Public disclosure
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 |
[Suggested description] Cleartext Storage of credentials in the iSmartAlermData.xml configuration file in the iSmartAlarm application through 2.0.8 for Android allows an attacker to retrieve the username and password. [VulnerabilityType Other] Cleartext Storage in a File or on Disk [Vendor of Product] iSmartAlarm [Affected Product Code Base] iSmartAlarm - <= 2.0.8 [Affected Component] iSmartAlermData.xml [Attack Type] Physical [Impact Information Disclosure] true [Attack Vectors] Extraction of iSmartAlermData.xml by any mean [Has vendor confirmed or acknowledged the vulnerability?] true [Discoverer] Francesco Servida (University of Lausanne) [Reference] https://francescoservida.ch/ http://blog.francescoservida.ch/2018/10/31/cve-2018-16222-to-16225-multiple-vulnerabilities-in-qbee-and-ismartalarm-products https://unil.ch/esc/ |
[CVE-2018-16223] Insecure Cryptographic Storage of credentials – QBee Camera Application (Android)
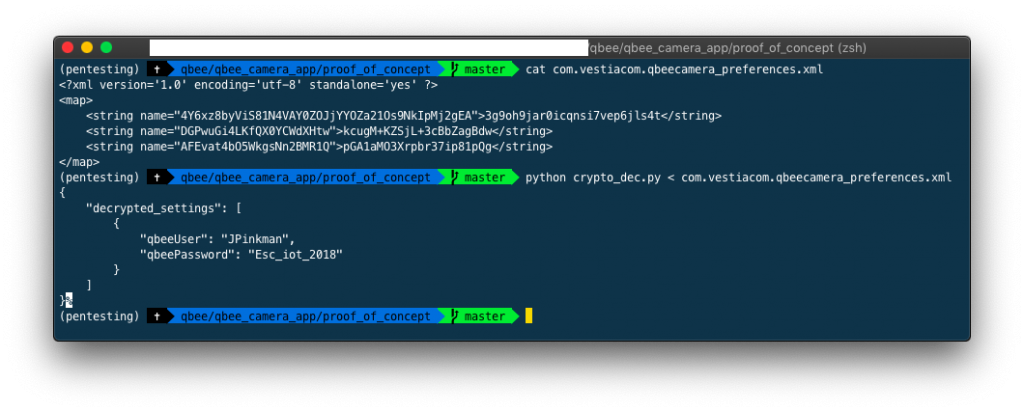
This second vulnerability also concerns the storage of user cloud credentials in the XML settings of the application, in this case of the QBee Camera Application.
Although the QBee Cam credentials were encrypted, the encrypted settings were in a format suggesting the use of the common “Secure Preferences” library. By default, this library stores the AES key alongside the encrypted data in the XML file. However, none of the values was a valid AES key for the decryption. Analysis of the android application revealed that the function handling the encryption/decryption was a slightly modified version of the “Secure Preferences” one. The AES key is in fact derived from the value in the file, by inserting a hardcoded string and hashing it with SHA 256. With that knowledge it was possible to implement a decryption function in python.
An attacker with physical access to the user device can extract the configuration file from the QBee Camera application.
Using the derived key, the attacker is able to decrypt the configuration file and extract the username and password.
- CVSS
- Base Score: 6.4
- Vector: AV:P/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H
- Impact Score: 5.9
- Exploitability Score: 0.5
Timeline
08.06.2018 – Vendor contacted (QBee)
03.07.2018 – Received response from Vestiacom (QBee) CEO, following communication problems & disclosure to Vestiacom
30.08.2018 – CVE-ID obtained from MITRE
30.08.2018 – Vulnerability disclosure date postponed from 9th September to 16th September following Swisscom request
18.09.2018 – Vestiacom confirms the patched version of QBee Cam has been submitted by Askey to Android’s Google Play.
31.10.2018 – Public disclosure
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 |
[Suggested description] Insecure Cryptographic Storage of credentials in com.vestiacom.qbeecamera_preferences.xml in the QBee Cam application through 1.0.5 for Android allows an attacker to retrieve the username and password. [VulnerabilityType Other] Insecure Cryptographic Storage [Vendor of Product] Vestiacom [Affected Product Code Base] QBee Cam (Android) - <= 1.0.5 [Affected Component] com.vestiacom.qbeecamera_preferences.xml, secure_preferences library [Attack Type] Physical [Impact Information Disclosure] true [Attack Vectors] Extraction of com.vestiacom.qbeecamera_preferences.xml file by any mean [Has vendor confirmed or acknowledged the vulnerability?] true [Discoverer] Francesco Servida (University of Lausanne) [Reference] https://francescoservida.ch/ http://blog.francescoservida.ch/2018/10/31/cve-2018-16222-to-16225-multiple-vulnerabilities-in-qbee-and-ismartalarm-products https://unil.ch/esc/ |
[CVE-2018-16224] Incorrect access control for the diagnostic files of the iSmartAlarm Cube One
It was possible to intercept the diagnostic logs sent from the base station to the smartphone application.

As the diagnostic endpoint was not authenticated the collection process was later integrated in a Python script in order to directly receive the data instead of having to intercept the stream to the smartphone application.
The vulnerability requires the attacker to have access to the local network on which the device resides.
The attacker is able to obtain a copy of the diagnostics logs from the CubeOne device without authentication needed.
The logs contain sensible information such as the interaction the user had with the cube one or the sensor logs. Other sensible information could be present but has not been studied.
- CVSS
- Base Score: 4.3
- Vector: AV:A/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N
- Impact Score: 1.4
- Exploitability Score: 2.8
Timeline
08.06.2018 – Vendor contacted
28.06.2018 – Established contact and disclosure to vendor
30.08.2018 – CVE-ID obtained from MITRE
24.09.2018 – iSmartalarm requests to postpone publication
31.10.2018 – Public disclosure
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 |
[Suggested description] Incorrect access control for the diagnostic files of the iSmartAlarm Cube One through 2.2.4.10 allows an attacker to retrieve them via a specifically crafted TCP request to port 12345 and 22306, and access sensitive information from the device. [Vulnerability Type] Incorrect Access Control [Vendor of Product] iSmartAlarm [Affected Product Code Base] iSmartAlarm Cube One - <= 2.2.4.10 (Fixed version number not yet available) [Affected Component] Network Traffic, Diagnostic Informations [Attack Type] Remote [Impact Information Disclosure] true [Attack Vectors] A carefully crafted TCP request to port 12345 et 22306 [Has vendor confirmed or acknowledged the vulnerability?] true [Discoverer] Francesco Servida (University of Lausanne) [Reference] https://francescoservida.ch/ http://blog.francescoservida.ch/2018/10/31/cve-2018-16222-to-16225-multiple-vulnerabilities-in-qbee-and-ismartalarm-products https://unil.ch/esc/ |
[CVE-2018-16225] Incorrect access control for the diagnostic files of the iSmartAlarm Cube One
- CVSS
- Base Score: 6.4
- Vector: AV:A/AC:H/PR:N/UI:N/S:U/C:L/I:L/A:H
- Impact Score: 4.7
- Exploitability Score: 1.6
